The Evolving Cyber Threat Landscape
Modern enterprises operate in highly interconnected digital ecosystems where applications, APIs, cloud platforms, and third-party vendors are deeply integrated. This complexity has expanded the attack surface far beyond traditional network perimeters. Cybercriminals now exploit software dependencies, open-source libraries, and vendor access points to infiltrate organizations silently. High-profile supply chain attacks have proven that a single compromised component can impact thousands of businesses at once. As a result, organizations can no longer rely on implicit trust models or perimeter-based defenses to secure their IT environments.
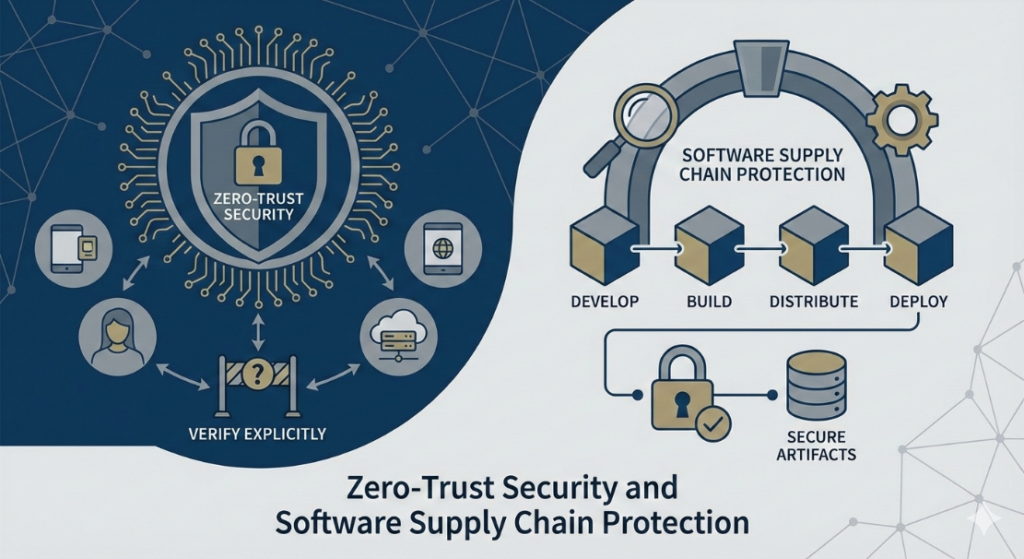
Understanding the Zero-Trust Security Model
Zero-Trust Security is based on a simple yet powerful principle: never trust, always verify. Instead of assuming that users, devices, or applications inside the network are safe, zero-trust enforces continuous authentication and authorization. Every access request is evaluated based on identity, device posture, location, and behavior. This approach significantly reduces lateral movement within systems and limits the potential damage of breaches. In the context of modern B2B IT environments, zero-trust has become a foundational security framework rather than an optional upgrade.
Why Software Supply Chains Are Prime Targets
Software supply chains involve multiple stakeholders, including developers, vendors, cloud providers, and open-source communities. Each dependency introduces potential vulnerabilities that attackers can exploit. Malicious code can be injected during development, updates, or distribution phases, often remaining undetected until it causes widespread damage. Since enterprises increasingly rely on third-party software to accelerate innovation, attackers focus on compromising trusted suppliers rather than targeting individual organizations directly. This shift makes supply chain security a critical priority for IT leaders.
The Intersection of Zero-Trust and Supply Chain Security
Zero-trust principles directly address many software supply chain risks by eliminating implicit trust at every stage of the software lifecycle. Applying zero-trust to supply chains means verifying the identity and integrity of code, users, and systems continuously. It ensures that access to repositories, CI/CD pipelines, and deployment environments is tightly controlled and monitored. By segmenting environments and enforcing least-privilege access, organizations can contain breaches and prevent compromised components from spreading across the enterprise.
Securing the Development and Deployment Pipeline
Modern DevOps and CI/CD pipelines require robust security controls to prevent tampering. Zero-trust enforces strict authentication for developers, automated tools, and service accounts accessing code repositories. Continuous validation of code integrity through cryptographic signing and checksum verification helps ensure that only trusted software is deployed. Additionally, real-time monitoring and anomaly detection can identify suspicious activities early in the pipeline, reducing the risk of malicious code reaching production environments.
Visibility and Continuous Monitoring Across Systems
One of the strongest advantages of zero-trust security is enhanced visibility. Organizations gain granular insight into who is accessing what, when, and why. This visibility is essential for detecting unusual behavior within software supply chains, such as unexpected code changes or unauthorized access to build systems. Continuous monitoring allows security teams to respond proactively rather than reactively. When combined with advanced analytics and automation, zero-trust enables faster incident response and minimizes business disruption.
Regulatory Compliance and Industry Standards
Governments and regulatory bodies are increasingly emphasizing supply chain security and zero-trust adoption. Compliance frameworks now require organizations to document vendor risk assessments, secure development practices, and access control policies. Zero-trust aligns naturally with these requirements by enforcing identity verification, audit trails, and security transparency. Organizations that adopt zero-trust not only improve their security posture but also gain a competitive advantage by demonstrating trustworthiness to customers and partners.
Business Value Beyond Cybersecurity
Zero-trust security and software supply chain protection deliver benefits beyond risk reduction. They enable secure collaboration with partners, faster digital transformation, and improved customer confidence. By reducing the blast radius of security incidents, businesses can maintain operational resilience even during attacks. Over time, zero-trust reduces the cost of breaches, downtime, and reputational damage, making it a strategic investment rather than a defensive expense.
Key Practices for Zero-Trust Software Supply Chain Protection
- Enforce strong identity verification for all users and service accounts
- Apply least-privilege access across development and deployment environments
- Continuously validate software integrity using code signing and checksums
- Monitor CI/CD pipelines for anomalies and unauthorized changes
- Segment networks and systems to limit lateral movement
- Perform regular vendor and third-party risk assessments
- Automate security policies and compliance reporting
Conclusion
Zero-trust security is no longer a future concept—it is a necessity in today’s interconnected software-driven world. As software supply chains grow more complex and attack methods become more sophisticated, implicit trust creates unacceptable risk. By integrating zero-trust principles into every layer of the software lifecycle, organizations can significantly reduce vulnerabilities, improve resilience, and protect their digital ecosystems. Ultimately, zero-trust combined with robust supply chain protection enables businesses to innovate securely while maintaining trust with customers, partners, and regulators.

